CTG Secure Stack™
Enterprise-Level Security, Without the Hassle
No minimum employees.
No high fees.
Just powerful, easy-to-use protection.
At CTG, we believe cybersecurity should be accessible and hassle-free.
Get top-tier security for your email, mobile, and browser trusted by global leaders.
Onboarding is fast & most clients are protected within 24 hours of their consultation
Simple. Secure. Smart.
Whats included below
-
AI-Powered Phishing & Malware Protection – Blocks advanced phishing, BEC (Business Email Compromise), and ransomware before they reach inboxes.
Account Takeover Prevention – Detects compromised accounts and prevents unauthorized access with real-time monitoring.
Zero-Day Threat Defense – Uses advanced sandboxing and behavioral analysis to stop new and unknown email threats before they spread.
-
Phishing & Credential Theft Prevention – Blocks malicious sites, stopping phishing attempts and credential harvesting attacks.
Zero Trust Access for SaaS & Cloud Apps – Ensures only authorized users can access sensitive business applications.
Seamless User Experience – Works in the background without slowing down browsing, ensuring secure and productive online access.
-
is a next-generation cybersecurity solution that combines networking and security into a single cloud-delivered service. It ensures secure and fast access to the internet, SaaS applications, and private apps — from anywhere, on any device.
Built on Check Point’s industry-leading threat prevention, SASE protects remote users, branch offices, and mobile workforces with zero trust access, cloud-native firewall, advanced threat intelligence, and secure web gateway all managed from a unified console.
-
Comprehensive Mobile Threat Defense – Prevents malware, network attacks, and device vulnerabilities in real time.
Zero-Touch Deployment – Easy, scalable protection that works across iOS & Android with minimal IT involvement.
On-Device Protection – Unlike cloud-only solutions, threats are stopped before they can compromise the device, ensuring offline security.
Introducing Our Exclusive Cybersecurity Package Collection - USA ONLY
Powered by High Wire Networks | Delivered by Cyber Tech Guardians
We’re proud to announce our strategic partnership with High Wire Networks (USA)—a trusted leader in managed cybersecurity services to bring you three exclusive cybersecurity packages tailored for modern businesses at every stage of growth.
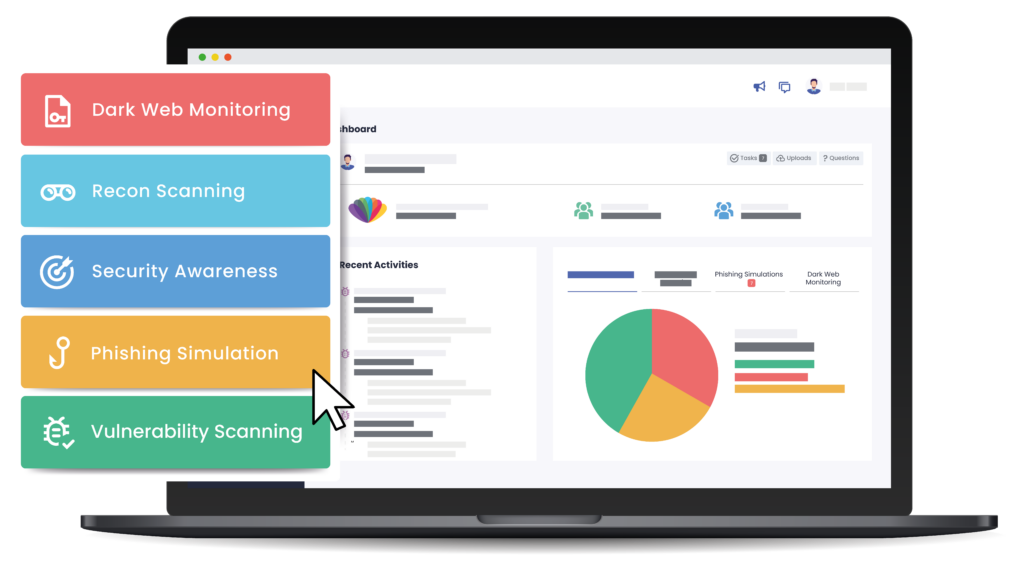
Introducing CTG WATCHTOWER
The early warning system for cybersecurity risks.
Our all in one Risk Management platform
A combination of some of our most powerful security tools, Threat Detect provides you with all the information you need to act decisively and secure your environment.
This unique bundle provides unrivalled visibility across your entire attack surface, identifying weaknesses in your environment, discovering hidden and unmanaged assets, and understanding how much of your information is already in the hands of bad actors.
Uncover Your Entire Attack Surface
Identify every online asset and get the full picture of your attack surface
Keep Your Ear to the Ground
Monitor every corner of the internet for stolen business credentials
Stay a Step Ahead of Attackers
Manage security vulnerabilities before they can be exploited
You deserve the best security with less headache