Enhance Your Cyber Resilience
Introducing CTG Watchtower
The early warning system for cybersecurity risks.
A combination of some of our most powerful security tools, Threat Detect provides you with all the information you need to act decisively and secure your environment.
This unique bundle provides unrivalled visibility across your entire attack surface, identifying weaknesses in your environment, discovering hidden and unmanaged assets, and understanding how much of your information is already in the hands of bad actors.
Uncover Your Entire Attack Surface
Identify every online asset and get the full picture of your attack surface
Keep Your Ear to the Ground
Monitor every corner of the internet for stolen business credentials
Stay a Step Ahead of Attackers
Manage security vulnerabilities before they can be exploited
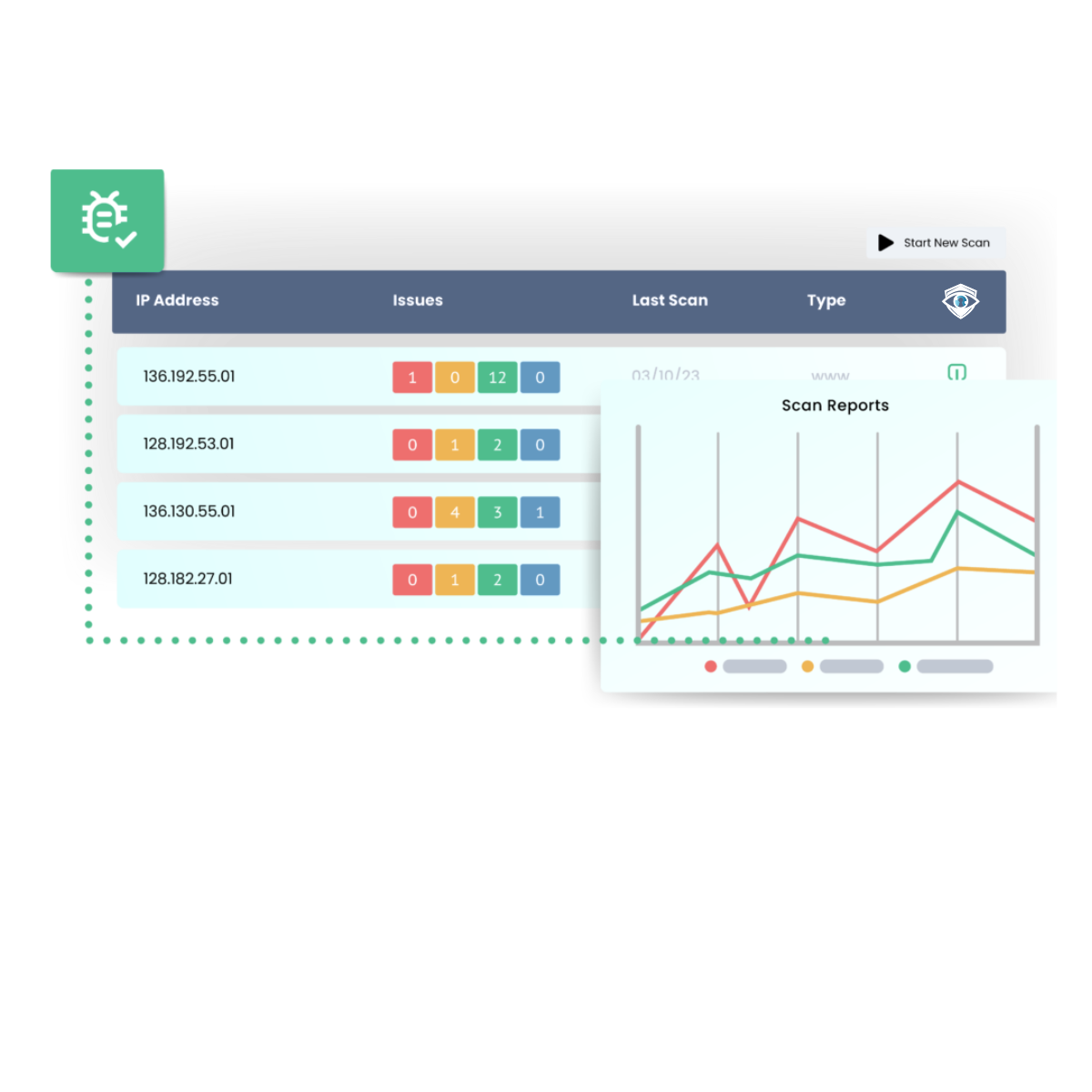
CTG WatchTower gives you real-time visibility into your vulnerabilities, helping you detect risks before attackers do.
Our continuous scanning engine monitors public IPs, web applications, and internal systems every 24–48 hours, delivering expert remediation advice directly to your dashboard.
No manual checks, no delays — just clear, actionable insights to strengthen your cyber resilience.
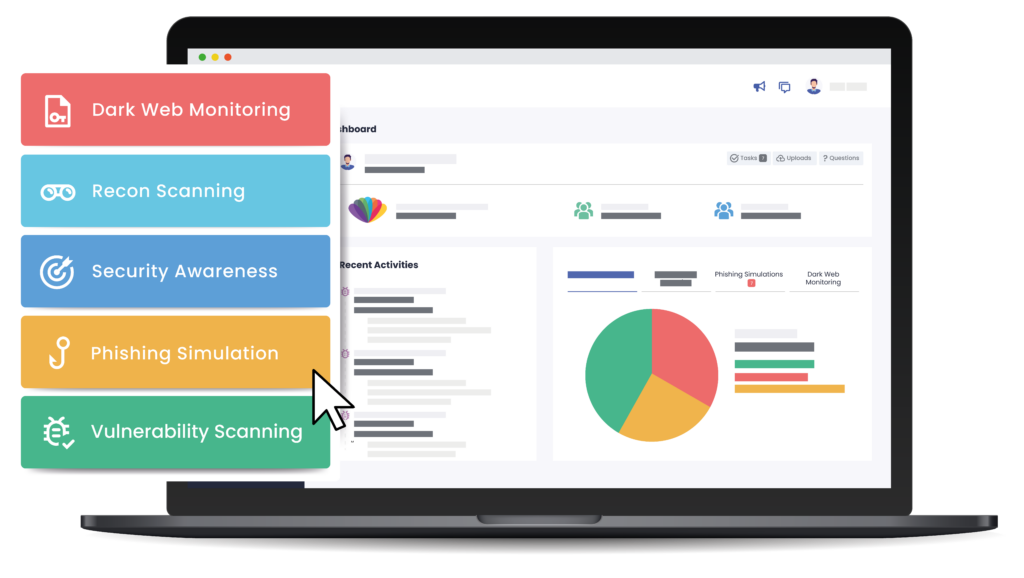
Your All-in-One Cyber Risk and Compliance Hub
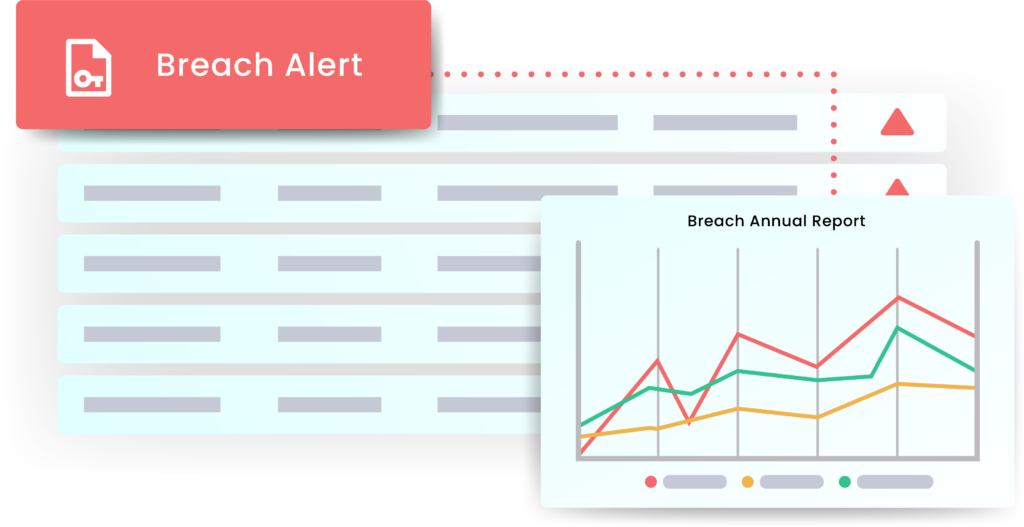
Dark Web Monitor
Find and fix breaches before impact.
-
WatchTower checks if employee emails, passwords, or company information appear in dark web breaches.
-
Get instant notifications if your data is found, and act before attackers exploit it.
-
Description text goes here
Stay informed about exposed data before attackers weaponize it.
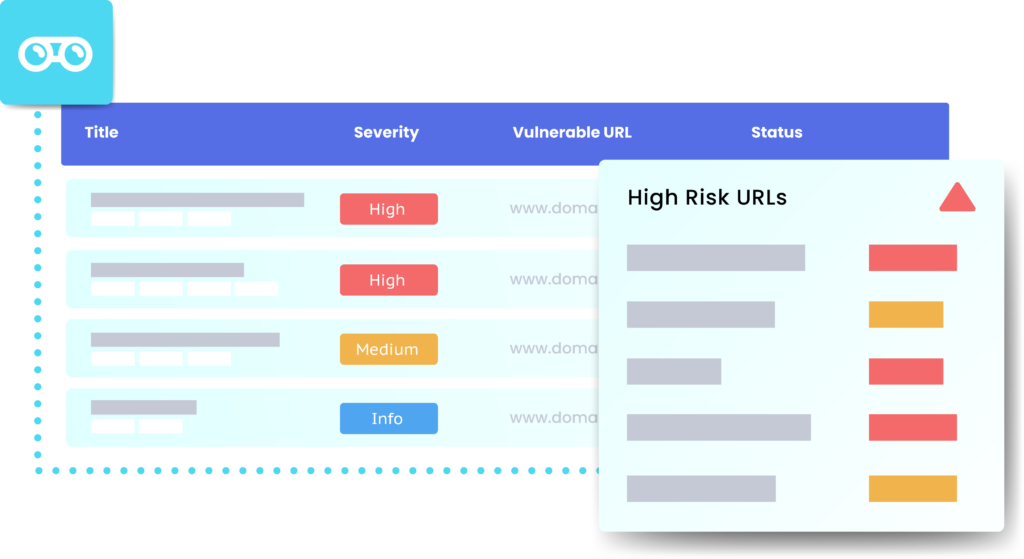
Recon scan
(Attack surface management)
Map, manage, and minimize your attack surface.
-
Recon Scan identifies all public-facing assets tied to your domain — even forgotten ones.
-
Scans discovered assets for weaknesses, misconfigurations, and missing patches.
-
identifies weaknesses like an attacker would — before they do.
Uncover hidden risks across your external attack surface and shut doors before attackers find them
Security Awareness Training
Reduce human error in your cyber security.
-
Every user starts with a cyber awareness questionnaire to personalize training paths.
-
New, targeted training modules delivered automatically every two weeks (or at your chosen frequency).
-
Includes fraud prevention, social engineering, social media security, and device protection.
Turn human error into human strength with intelligent, ongoing security awareness training.
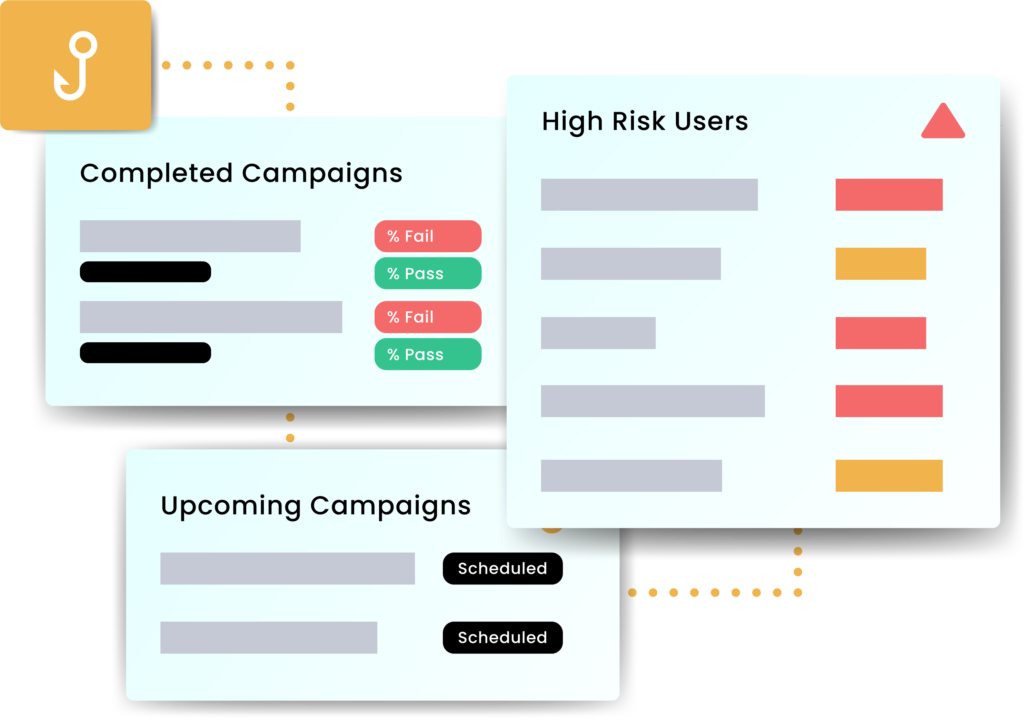
Phishing Simulation
Empower your people to identify phishing attacks.
-
Use a bank of real phishing attack templates, not fake ones
-
Campaigns don’t all hit at once — emails are delivered randomly to mimic real attack patterns.
-
Train employees to recognize and respond correctly, not just pass a test.
Strengthen your human firewall with realistic phishing simulations and smarter training.
Vulnerability Scan
-
Continuous assessment of public IPs, web apps, and internal devices.
-
Set your assets once — WatchTower monitors continuously without the need for repeated consultations.
-
Get clear next steps for fixing vulnerabilities, not just technical scan reports.
Monitor vulnerabilities continuously — fix them faster with expert-guided remediation
Stay a step ahead of attackers.